Blog Posts In Category: IT Strategy
When you get a text with a verification code, it usually means a service wants to confirm your identity during a login or transaction. If you didn’t ask for the code, it probably means someone else is trying to get into an account connected to you. These messages can be legitimate security tools, but scammers…
When you sign in to services using HealthSafe ID (HSID), you’ll usually get an access code or verification code. These codes confirm your identity and help block unauthorized access. HSID access codes and verification codes add an extra security layer that keeps your accounts safer from compromise. It might seem like you’re just typing in…
If you see an “upload blocked” error in SharePoint or OneDrive, it usually means your Microsoft 365 apps and OneDrive are signed in with different accounts. The quickest fix? Make sure you’re signed into both OneDrive and your Office apps with the same account. That step alone solves the problem most of the time. Sometimes,…
When it comes to storing business files in Microsoft 365, most teams end up choosing between SharePoint and OneDrive. Both are solid options, but they really serve different needs. If you want a spot for personal file storage, OneDrive fits the bill. SharePoint, though, works better for team collaboration and shared projects. We talk to…
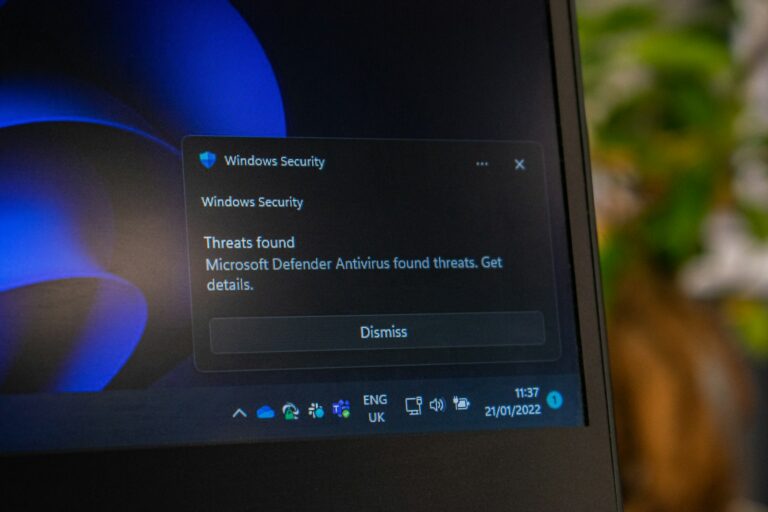
A lot of small business owners wonder if Microsoft Defender alone can keep their systems safe. For most small businesses, Microsoft Defender for Business does a solid job as the main antivirus solution. It brings threat detection, ransomware protection, and endpoint security—definitely a step up from the basic antivirus tools you’ll find in Windows. Still,…
When Office 365 gets stuck during installation, it can really feel like nothing’s moving forward. Usually, the problem comes from system processes, your internet connection, or security settings messing with the setup. The upside? Most of these issues have simple fixes, so you don’t need to sit around forever waiting for that progress bar. We…
Trying to sign in to Office 365 with the right password, but still getting blocked? That’s annoying, and it happens more often than you’d think. Usually, the culprit isn’t the password itself. Instead, cached credentials, account sync hiccups, or outdated authentication settings tend to cause these headaches. The upside? You can usually spot and fix…
When Microsoft Office flashes a “not licensed” or activation error, it can throw a wrench in your day—especially if you need Word, Excel, or Outlook right away. Usually, this message pops up because your subscription expired, your account isn’t linked right, or the software didn’t activate properly. The upside? Most of these problems have a…
When Microsoft Teams messages just won’t load or calls drop out of nowhere, it throws a wrench into your day and slows everyone down. Usually, these headaches come from network hiccups, software bugs, or devices that just aren’t playing nice—but with the right troubleshooting, you can sort most of them out. Figuring out what’s causing…
When Office documents won’t sync with OneDrive, it throws a wrench into your workflow and adds a layer of frustration nobody needs. Usually, the main culprits are issues with the OneDrive sync client, hitting storage limits, or network problems that stop files from updating the way they should. Figuring out why this happens is the…